GP.Data Zone Protection
| Page maturity This page has maturity level 4 (mature) |
| GP | Data Zone Protection | Version: | 0.3 | 
| |
|---|---|---|---|---|---|
| Document type: | Generic Pattern | Owner: |
| This Pattern realizes a security separation between different Data Transport zones. |
Description
This Generic Pattern belongs to "Core". Two or more data transport zones may need to be separated because of different security-related requirements. If this is the case, then traffic from one zone traveling to the other zone needs to be processed so as to satisfy the security requirements imposed by the separation. To this end, this pattern may be employed. In practice, use of this pattern often leads to use of a firewall device, but as security requirements evolve, so may the realization of this pattern.
Services realized
This Pattern realizes the following service(s):
- Data Zone Protection (This service satisfies relevant security requirements while passing data between different Data Transport services.)
Functional and Integration view
This is the graphic representation of the functional model of this Generic Pattern:
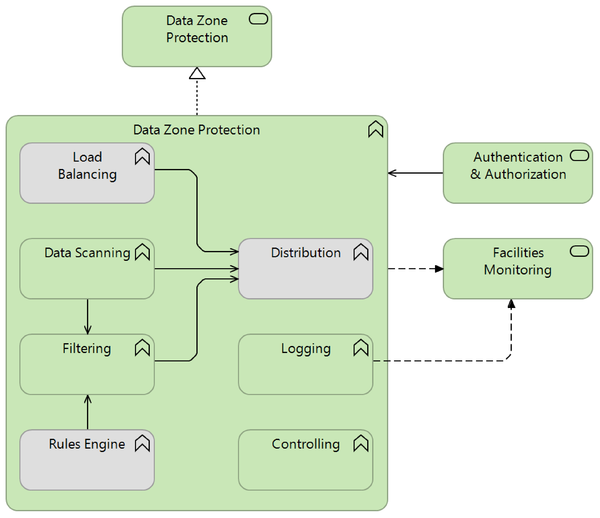

Generic Pattern Composition
This pattern is an aggregation of the following (mandatory and optional) functions, expressed in Generic Functions:
| Icon | Function | Inclusion | Rationale |
| Filtering | recommended | This function performs the actual filtering of data flowing from one data zone to the other. The filtering is based on criteria that are derived from the security requirements, e.g. "no traffic is allowed from the DMZ to the internal network, with the exeption of ...". | |
| Load Balancing | optional | Since this Pattern often is used as a chokepoint where all data traffic must go through, it may be necessary to include Load Balancing to provide higher availability of this Pattern. | |
| Data Scanning | recommended | When filtering based on traffic characteristics does not suffice, filtering based on data (content, deep inspection) may be needed. This can be useful for securing message exchange between zones (e.g. e-mail or SOAP messages), but also for deep inspection in certain protocols. This can for example detect malicious commands inside protocol packets, e.g. SQL injection instructions inside a HTTP request. When data scanning reveals a problem, a fitting action must be undertaken by another function (e.g. the Filter may drop the packet or block the sender, or Monitoring may issue an alert). | |
| Rules Engine | optional | This function enables the processing of more complex logic, such as the well-known "firewall rules".
Note that the rules may be stored in the Data Zone Protection facility itself, or outside of it, with deployment to this facility. | |
| Logging | recommended | Since this Pattern is used for security purposes, this function is required to provide security personnel with the necessary logs for security monitoring and auditing. | |
| Distribution | optional | Since this Pattern often is used as a chokepoint where all data traffic must go through, it is also a good point to locate Distribution. | |
| Controlling | recommended | Access to the configuration and operation of this security related Pattern is most always restricted. |
Services connected with this Generic Pattern
This Generic Pattern has the following mandatory and optional relations with adjacent Generic Services.
| Service | Adjacency | Summary | Rationale |
| Authentication & Authorization | optional | This service can validate an identity claim, and it can validate the permissions required for an action, as part of an Authentication & Authorization process. | The Authentication & Authorization Pattern can be linked to this Pattern when this Pattern is to support authorization (and/or authentication), so as to feed the Traffic Filter facility with the results of identity and/or permission validations. |
| Facilities Monitoring | optional | This service allows its users to monitor IT facilities with the aim of guarding operational continuity or security. | Transport Zone Protection is usually employed to enforce security levels within one or more Data Transport Zones; thus, many events that occur in a Transport Zone Protection facility are of interest to the security officers. This means it is very desirable to have the facility report directly to (a Security instance of) Facilities Monitoring. |
Applied Patterns based on this Generic Pattern
The following Applied Patterns are based wholly or in part on this Generic Pattern: